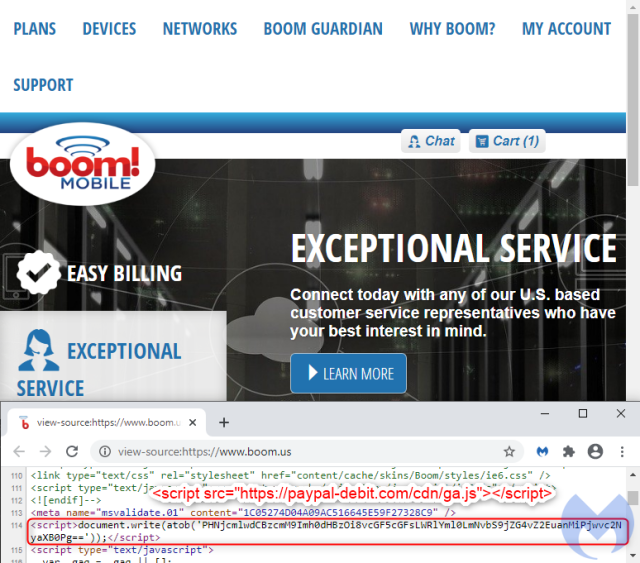
Enlarge (credit: Getty Images)
Hackers sponsored by the Russian and North Korean governments have been targeting companies directly involved in researching vaccines and treatments for COVID-19, and in some cases, the attacks have succeeded, Microsoft said on Friday.
In all, there are seven prominent companies that have been targeted, Microsoft Corporate VP for Customer Security & Trust Tom Burt said. They include vaccine makers with COVID-19 vaccines in various clinical trial stages, a clinical research organization involved in trials, and a developer of a COVID-19 test. Also targeted were organizations with contracts with or investments from governmental agencies around the world for COVID-19-related work. The targets are located in the US, Canada, France, India, and South Korea.
“Microsoft is calling on the world’s leaders to affirm that international law protects health care facilities and to take action to enforce the law,” Burt wrote in a blog post. “We believe the law should be enforced not just when attacks originate from government agencies but also when they originate from criminal groups that governments enable to operate—or even facilitate—within their borders. This is criminal activity that cannot be tolerated.”
Read 6 remaining paragraphs | Comments
from Biz & IT – Ars Technica https://ift.tt/2H38aHy
via A.I .Kung Fu